File system details View: All details (Selection)-Adds the folder C: Program Files (x86) Cokcultprasitain Adds the file Plgaghtatumusyhlp. Dll '=' 8 / 12 / 2016 8: 41 AM, 249344 bytes, A Adds the file SoEasy. Exe '=' 8 / 12 / 2016 8: 41 AM, 803472 bytes, A Adds the file SpyProDll. Dll '=' 8 / 12 / 2016 8: 41 AM, 134656 bytes, A Adds the. Click one of the buttons below to download the Google Home app on your mobile phone or tablet. Tap the button below to download the Google Home app on the Play Store. Why have I posted these here? The Google Chrome Web Store is known for having malicious apps and extensions listed among the legitimate ones, so I have listed the proper links to a few of the popular ones.
Certain Google-owned domains have caused Chrome users, from even the most skilled researchers to regular users, to question whether they are malicious.
The domains I am referring to are redirector.gvt1.com and gvt1/gvt2 subdomains that have spun many questions on the internet.
After receiving multiple concerned questions over the years, BleepingComputer has dug deeper into the domains’ origin and whether they should be something to worry about.
What are these suspicious gvt1.com domains?
The domains *.gvt1.com and *.gvt2.com, along with their subdomains, are owned by Google and typically used to deliver Chrome software updates, extensions, and related content.
For example, when we started Chrome just now, it attempted to connect to the following domains:
However, these URLs and the domain name has repeatedly caused confusion among developers and researchers due to their suspicious-looking structure:
Likewise, gvt.1com domains have been previously flagged by antivirus products as malware [1, 2] and by researchers as an Indicator of Compromise (IOC) [1, 2, 3].
Moreover, the redirector.gvt1.comlinksredirect to an URL that contains the user’s IP address, among other elusive parameters which may cause further suspicion.
For example, BleepingComputer traced the following link, which redirects twice to much larger URLs with an arbitrary subdomain and extensive GET parameters, such as the user’s IP address:
http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNmRlQUFXU0o1UkNFTWx3aGRUUHBsWUJUZw/7819.902.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx
Should we be concerned about gvt1.com URLs?
This is where it gets complicated, but the answer is: no, but Google could secure them better.
The GVT in the gvt1.com domain stands for Google Video Transcoding, and is used as a cache server for content and downloads used by Google services and applications.
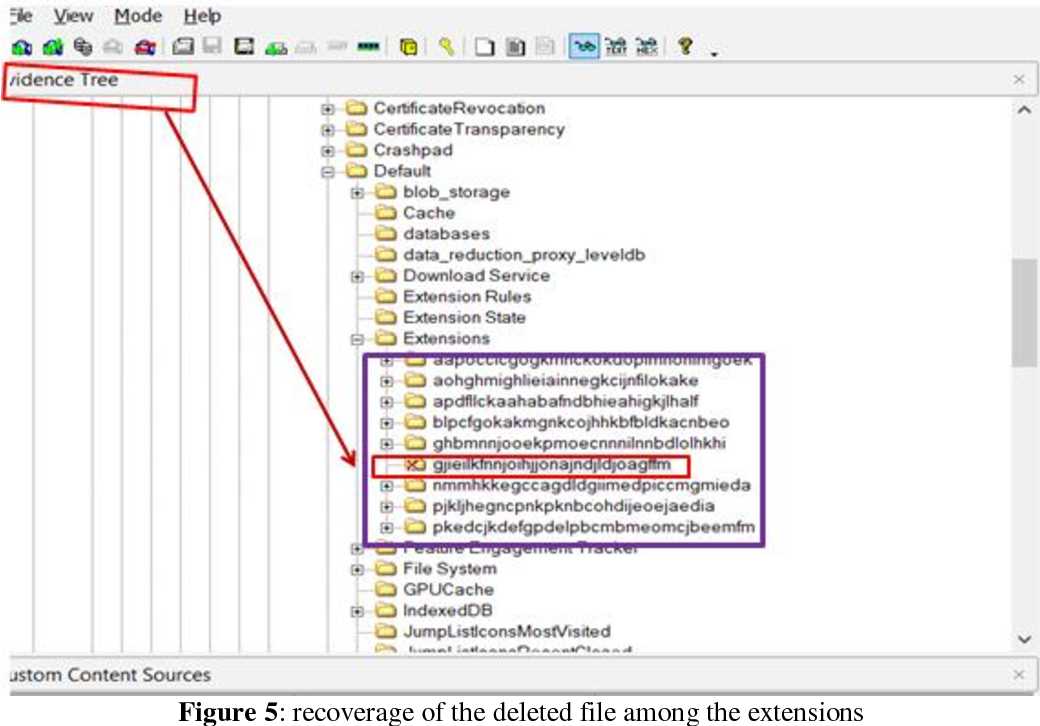
Pkedcjkdefgpdelpbcmbmeomcjbeemfm
Put simply, the *.gvt1.com domains are only used by Google to deliver official content, Chrome browser updates, and Android-related executables.
“redirector.gvt1.com is a redirection service used by Google for a variety of purposes, including download of updates, etc.,” Eric Lawrence, a former member of the Chrome Security Team, stated in a Google bug post.
Going back to the link analyzed in the previous section as an example, we can see the URL ending in .crx represents a Chrome extension :
http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNmRlQUFXU0o1UkNFTWx3aGRUUHBsWUJUZw/7819.902.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx
BleepingComputer traced the extension to be the Chrome Media Routerextension, a legacy component that was used by Chromecast.
What is concerning, is that Google continues to use the insecure HTTP protocol rather than HTTPS when connecting to these URLs.
By connecting to the URLs via HTTP, it may be possible to use man-in-the-middle (MiTM) attacks to modify the downloads in some manner. If you have malware installed that is intercepting HTTP traffic, you have more to worry about at this point.
In conclusion, when seeing traffic concerning *.gvt1.com or *.gvt2.com domains in your corporate network, it is not a cause for alarm but simply a legitimate Chromium download taking place.
However, Google should switch to using HTTPS to prevent potential MiTM attacks, and administrators should continue to follow best practices such as analyzing traffic from the URLs.
BleepingComputer reached out to Google multiple times well in advance, but we have not heard back before press time.
One of most obnoxious experiences that most new users of the Linux platform usually face is the inability to find the simplest and yet more effective means of looking up files on their system.
Linux, like almost any other operating system, utilizes several mechanisms to answer search queries for users. Two of the most popular file searching utilities accessible to users are called find and locate.
Chrome Extension Pkedcjkdefgpdelpbcmbmeomcjbeemfm
Now, it is important to note that both search processes work extremely well but nonetheless, the center of this article will be more on the locate utility, which is the more convenient of the two as it uses more efficient ways to quickly process queries inputted by the users.
The locate utility works better and faster than it’s find counterpart because instead of searching the file system when a file search is initiated – Something find does – locate would look through a database. This database contains bits and parts of files and their corresponding paths on your system.
Here are ten simple locate commands to set you up in becoming more productive with your Linux machine.
1. Using locate Command
Firing locate command to look for a file is pretty easy and straightforward. All you need to do is type:
2. Limit Search Queries to a Specific Number
You can limit your search returns to a required number to avoid redundancy with your search results using the -n command.
For example, if you want just 20 results from your queries, you can type the following command:
The results will show the first 20 files that end with .html.
Pkedcjkdefgpdelpbcmbmeomcjbeemfm/cast_sender.js
3. Display The Number of Matching Entries
If you want to display the count of all matching entries of file “tecmint“, use the locate -c command.
4. Ignore Case Sensitive Locate Outputs
By default, locate is configured to process queries in a case sensitive manner meaning TEXT.TXT will point you to a different result than text.txt.
To have locate command ignore case sensitivity and show results for both uppercase and lowercase queries, input commands with the -i option.
5. Refresh mlocate Database
Since locate command relies on a database called mlocate. The said database needs to be updated regularly for the command utility to work
efficiently.
To update the mlocate database, you use a utility called updatedb. It should be noted that you will need superuser privileges for this to work properly, is it needs to be executed as root or sudo privileges.
6. Display Only Files Present in Your System
When you have an updated mlocate database**, locate command still produces results of files whose physical copies are deleted from your system.
To avoid seeing results of files not present in your machine at the time of punching in the command, you will need to use the locate-e command. The process searches your system to verify the existence of the file you’re looking for even if it is still present in your mlocate.db.
7. Separate Output Entries Without New Line
locate command’s default separator is the newline (n) character. But if you prefer to use a different separator like the ASCII NUL, you can do so using the -0 command line option.
8. Review Your Locate Database
If you’re in doubt as to the current status of your mlocate.db, you can easily view the locate database statistics by using the -S command.
Extension Pkedcjkdefgpdelpbcmbmeomcjbeemfm
9. Suppress Error Messages in Locate
Constantly trying to access your locate database does sometimes yield unnecessary error messages stating that you do not have the required privileges to have root access to the mlocate.db, because you’re only a normal user and not the required Superuser.
To completely do away with these message, use the -q command.
Chrome Extension Ids
10. Choose a Different mlocate Location
If you’re inputting queries looking for results not present in the default mlocate database and want answers from a different mlocate.db located somewhere else in your system, you can point the locate command to a different mlocate database at a different part of your system with the -d command.
locate command might seem like one of those utilities that does everything you asked it to do without much of a hustle but in truth, in order for the process to keep its efficiency, the mlocate.db needs to be fed with information every now and then. Failure to do so might render the program a bit useless.
